How to protect smart machines from cybersecurity attacks
- January 30, 2025
- Best Practices
- Automation
Machines are smarter and more interconnected than ever, but they are more vulnerable to cybersecurity attacks. Bringing information technology (IT) and operational technology (OT) together and aligning goals will go a long way to creating a secure ecosystem.

Machines are getting smarter and more interconnected, which increases their potential for manufacturers. They’re not siloed off anymore, and they can provide more value to a manufacturer beyond their initial footprint. Smart machine integration and communications abilities require attention to cybersecurity.
“At the end of the day, everyone buys a machine to be more productive,” said Nivedita Ojha, VP of products, Fort Robotics, in her presentation “Cybersecurity for Smart Machines: Tackling the Real-World Risks,” at Automate 2023 in Detroit. “Whether you’re buying a machine for manufacturing, warehouses or construction… it’s all about productivity.”
However, many of these increased capabilities result from being connected to the internet. The industrial Internet of Things (IIoT) has many benefits, but these operational enhancements widen exposure to potential cyberattacks.
Manufacturers now face the constant specter of a cybersecurity attack. A successful hack or breach can go beyond losing data or intellectual property (IP). A manufacturing facility also could be affected by having its production lines damaged with unplanned downtime, and workers’ safety could be at risk.
Protecting against these risks and deploying machines in a connected worksite requires a new approach to security that requires information technology (IT) and operational technology (OT) to come together.
Disruptions can have a massive impact, Ojha said. Downtime can cost thousands per minute, and unplanned downtime is even more expensive. Asset maintenance can cost millions in lost revenue per incident, as well.
Is your business ready to handle a cyberattack?
Assess your organization’s cybersecurity preparedness and compare your score
to industry peers for key industrial security protections.
Bringing IT and OT together: Predictive, protective benefits
Ojha said one of the biggest challenges is that IT and OT have evolved, but they haven’t evolved together since IIoT devices were launched in industrial environments. There are millions of connected OT machines, but security is insufficient and reactive rather than predictive and protective. This lack of alignment, coupled with resistance to IT slowing down production lines with their priorities, has created friction between the two sides.
“In this rush to bring all these devices, IT hasn’t caught up to where it needs to,” she said. Everyone knows it’s required, but they haven’t come together to solve the problem, which has resulted in a Band-Aid approach.”
OT manager priorities
Ojha used a fictional example with an OT manager overseeing a warehouse to explain key priorities and IT’s role in bridging these gaps. More than anything, Ojha said, an OT manager wants to maximize productivity with minimal disruption.
The OT manager is responsible for:
- Deploying new machines to the OT network at scale
- Keeping the machine floor running smoothly
- Maintaining the machines
- Managing personnel restrictions and determining who can use what machines and where
- Meeting IT compliance requirements for the machines.
To adopt IT security requirements, the manager needs an OT solution that works like a mobile device management (MDM) solution that allows the manager to:
- Keep the worksite productive
- Prevent cybersecurity attacks and protect the business and its IP
- Ensure appropriate machine usage and access
- Control data flowing between machines, cloud and services
- Manage machines at scale.
Picking the right solution, Ojha said, helps the manager comply with IT priorities while still meeting OT productivity goals.
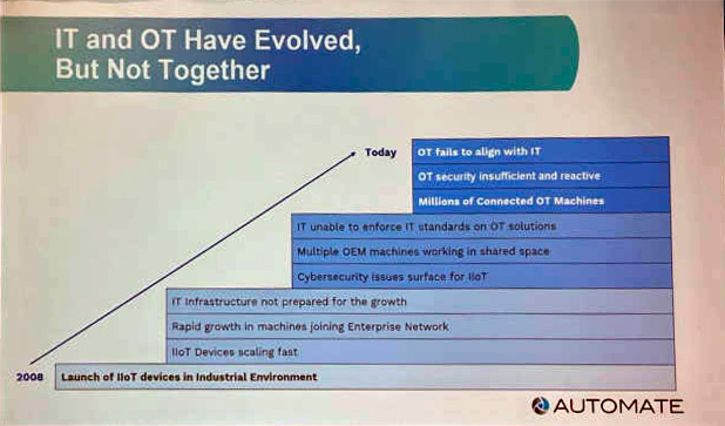
IT and OT have evolved, but they haven’t evolved together since IIoT devices were launched in industrial environments. Courtesy: Chris Vavra, CFE Media and Technology
Aligning and securing IT/OT priorities benefits all
Aligning OT with IT protects and secure machines while monitoring permissions and performance data. OT and IT collaboration also helps users preemptively respond to safety and security vulnerabilities as well as recovering from each event.
Ojha said, “It’s time to bridge the IT and OT worlds. You want to make sure you get access to similar data across the enterprise.”
Developing a secure machine platform will help in that by providing policy and permission enablement as well as providing monitoring and analytics.
Protect, minimize operational risks in 5 ways
Ojha highlighted five pillars that need protecting to minimize operational risks.
- Tamper-proof devices. Lock down devices and block them from tampering and modifying hardware.
- Secure boot. Securely starting up the device and prevent security threats from inserting during device boot-up.
- Secure configuration. Setting up devices. Block tampering with device settings and communication methods.
- Secure communication and data. Encrypt data and comms and prevent them from communication with unknown entities.
- Secure update. Update device firmware and block inserting security threats on devices.
While no system is perfect and depends on people following through, paying attention to these steps can help manufacturers come closer to securing a complete ecosystem.
Chris Vavra, web content manager, CFE Media and Technology, [email protected].
View the original article and related content on Control Engineering